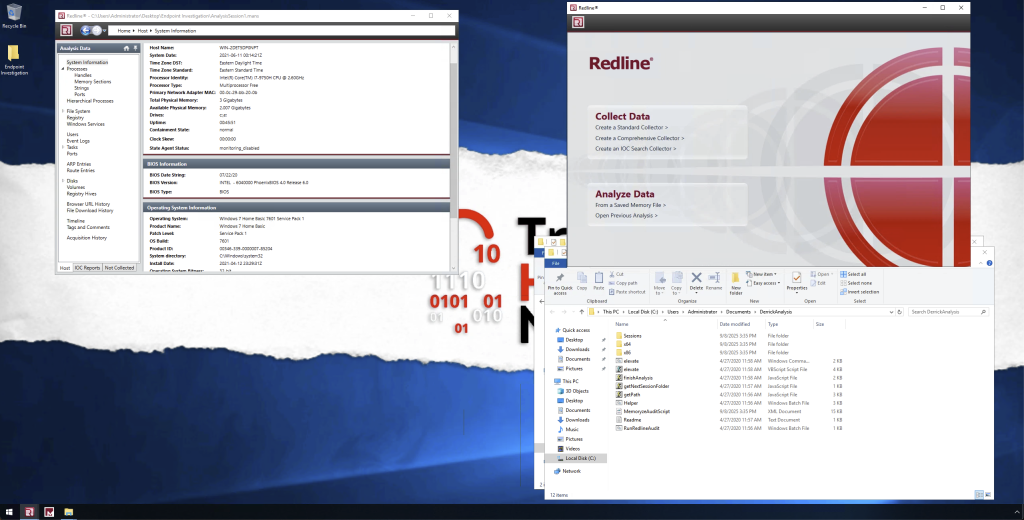
This room focused on using Redline, a memory forensics tool, to analyze systems for signs of malicious activity. I learned how to collect memory snapshots and investigate them for artifacts like processes, network connections, and loaded modules.
By practicing with Redline, I saw how memory analysis can uncover evidence that doesn’t persist on disk, such as injected code or in-memory malware. It reinforced why memory forensics is such a crucial part of modern investigations.